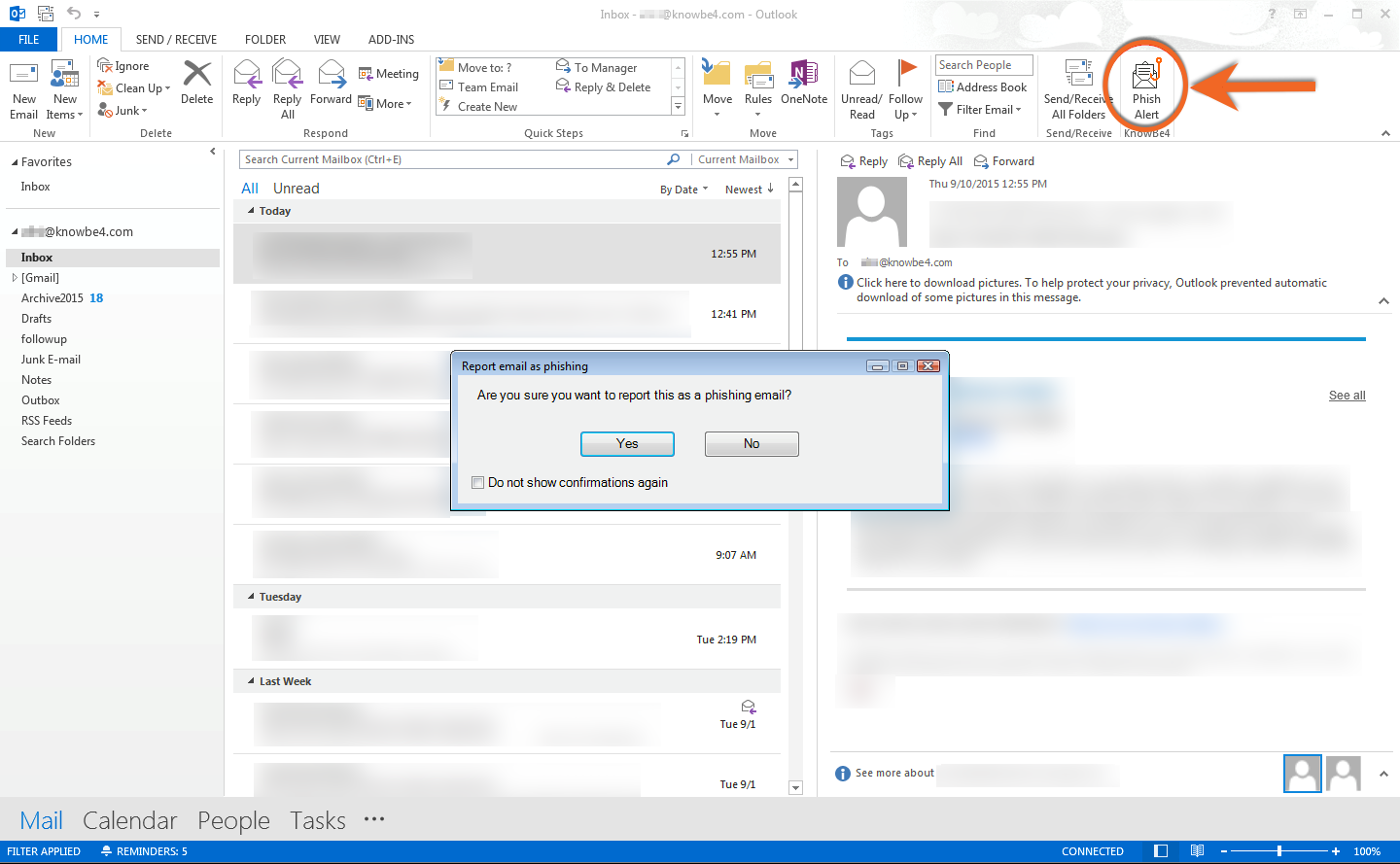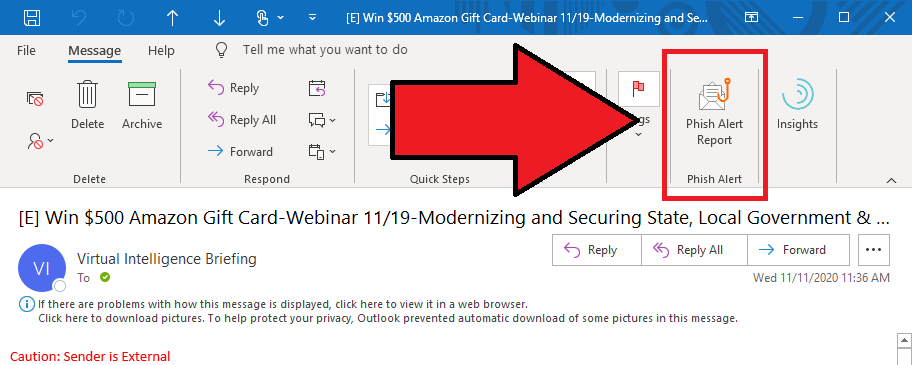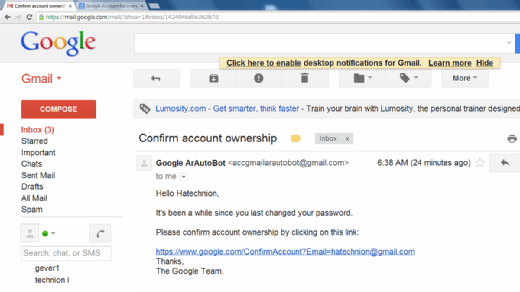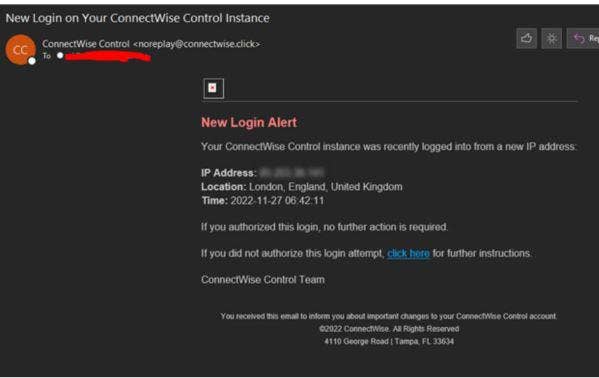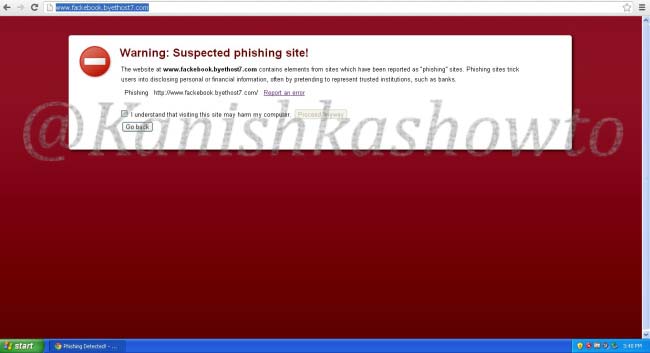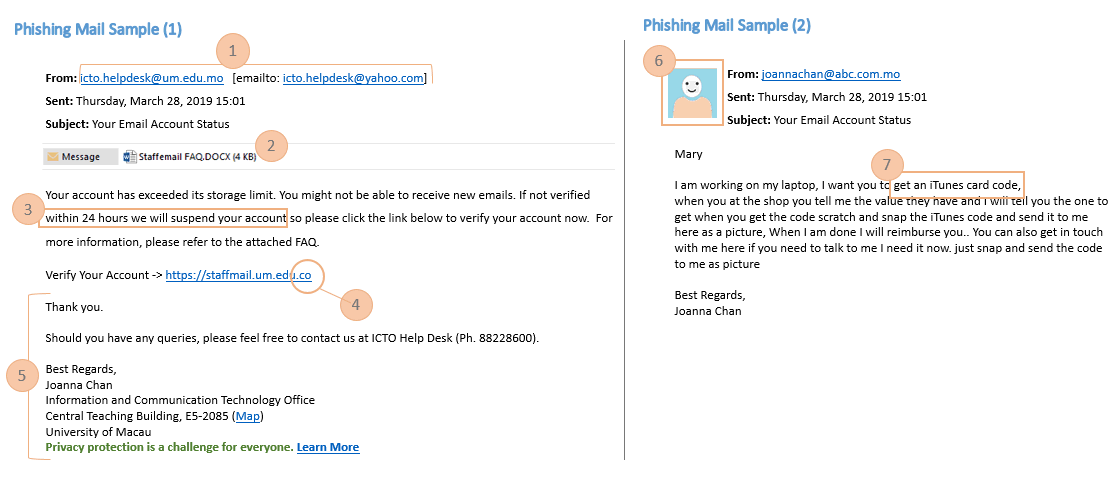
Information and Communication Technology Office (ICTO) | Beware of Phishing Trap | Information and Communication Technology Office (ICTO)

Phishing scam vector symbol with desktop computer, red credit card and fishing hook isolated on blue background. Flat design, easy to use for your website or presentation. Stock Vector | Adobe Stock

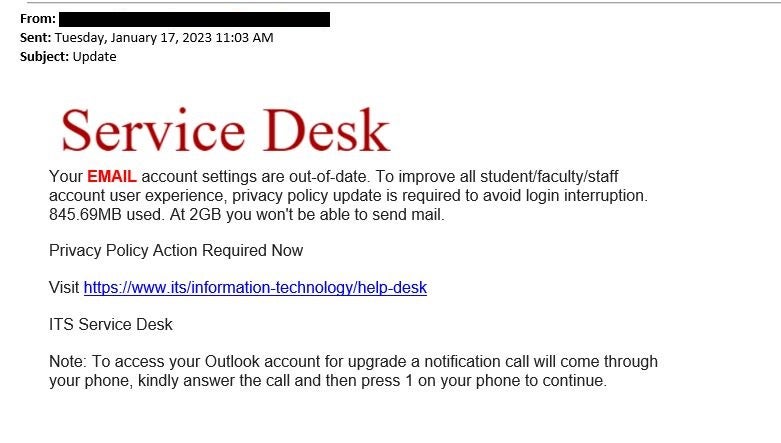
Phishing Alert: Quarantined Message Scam from “Support Desk” Includes Recipient's Email Address | Information Technology | University of Pittsburgh