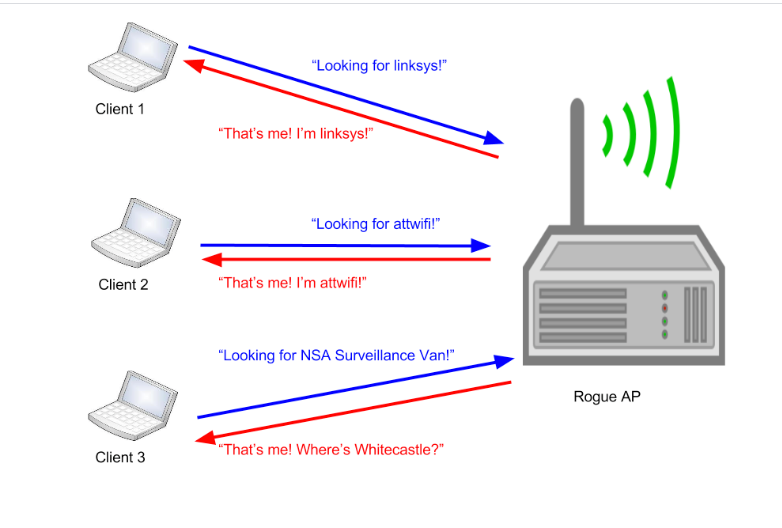
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members

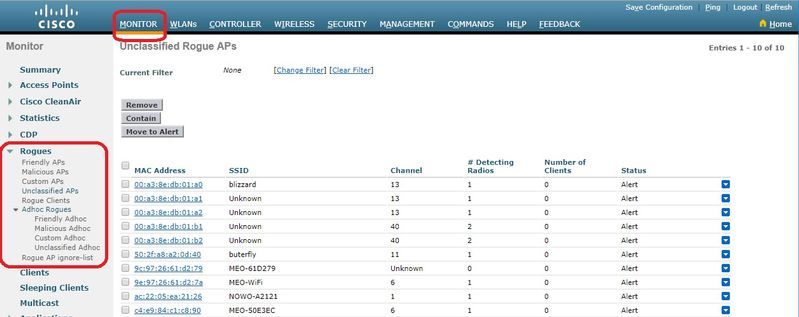
Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point
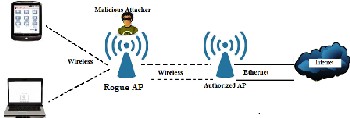
![Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17] | Download Scientific Diagram Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17] | Download Scientific Diagram](https://www.researchgate.net/publication/276230435/figure/fig3/AS:668979894951955@1536508644638/Unsecured-Rogue-Access-Point-Allows-Anyone-to-Connect-to-the-Network-17.jpg)
Unsecured Rogue Access Point Allows Anyone to Connect to the Network [17] | Download Scientific Diagram

Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text


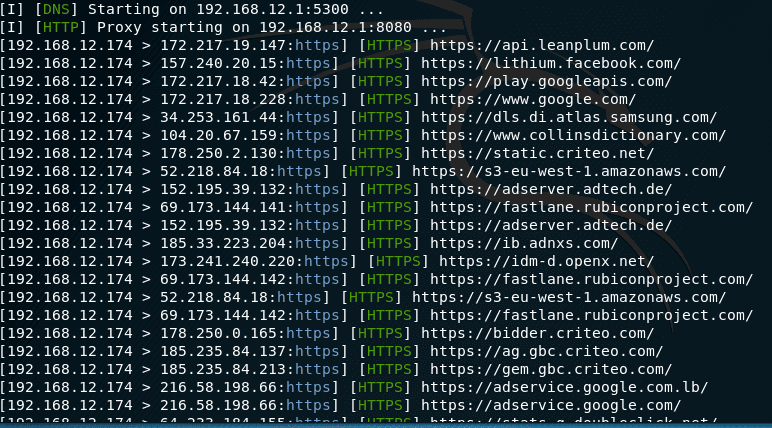
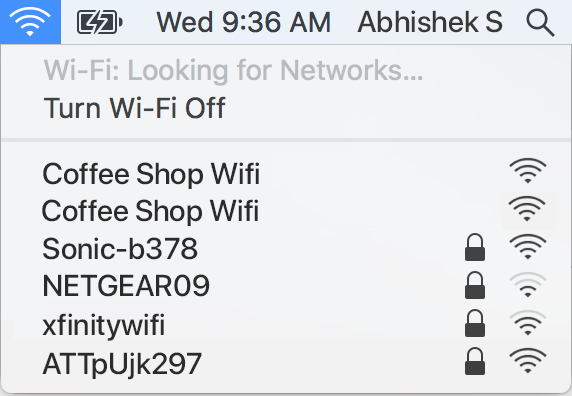
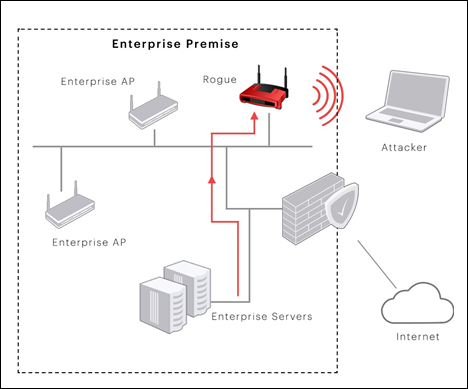
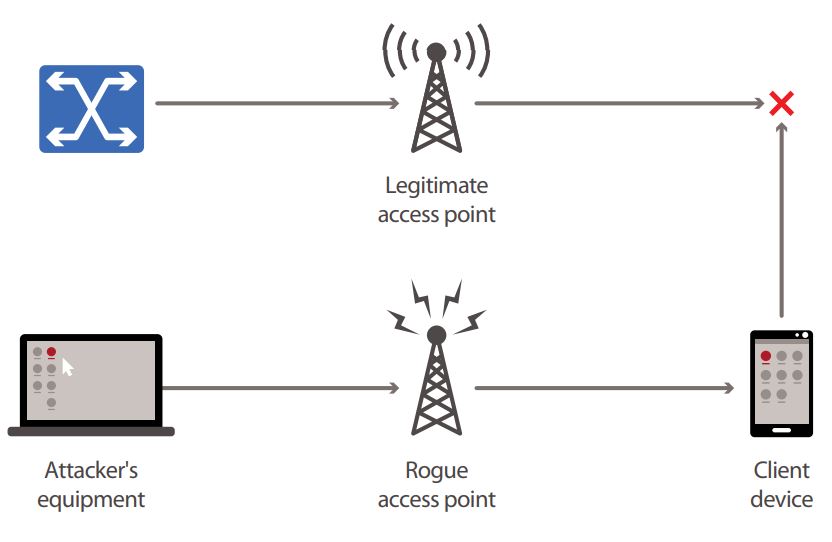




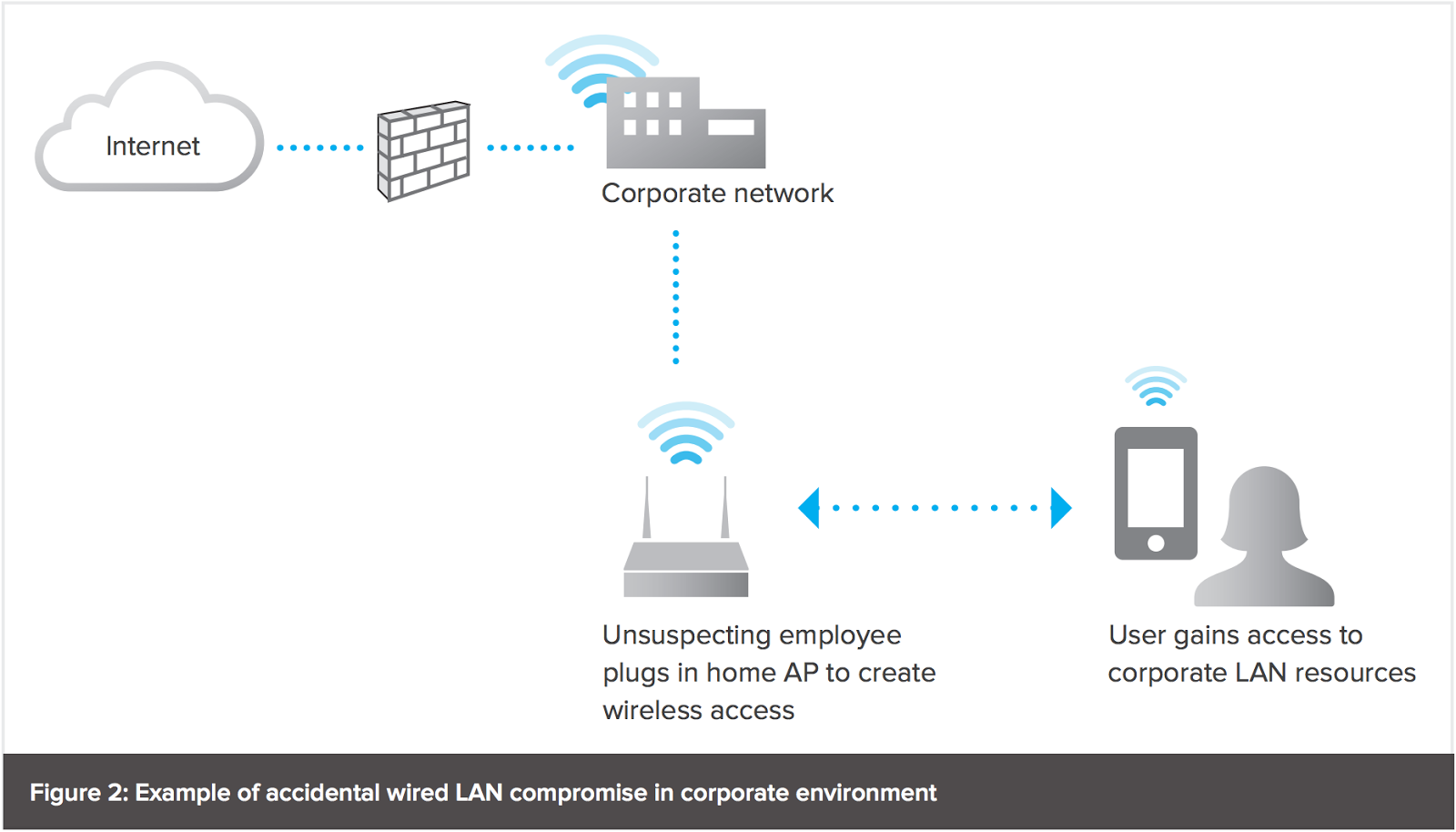






![PDF] Rogue Access Point Detection System in Wireless LAN | Semantic Scholar PDF] Rogue Access Point Detection System in Wireless LAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/41a44df312f08ce3551a932335310d6e542e2fa7/2-Figure1-1.png)